acatech am Dienstag: cybersecurity – challenges for critical infrastructure
Munich, 04 April 2023
Incidents such as the grounding of flights due to the accidental severing of fibre-optic cables and the hacking of the German parliament show that cybersecurity is an issue again and again, especially when it is lacking and the consequences are considerable. It is therefore worth thinking about cybersecurity in a new way, said IT researcher and acatech Executive Board member Claudia Eckert at acatech am Dienstag on 4 April. IT experts from Stadtwerke München and Deutsche Telekom gave real-life insights.
Whenever cyber attacks and accidents affect critical infrastructure such as hospitals or rail transport the consequences for society can be far-reaching. Comprehensive security is essential. In his introduction, acatech President Jan Wörner shed light on the various areas of security. There are three kinds of breach of security of infrastructure: sabotage, accidents and forces of nature. This is what makes the resilience of these structures so important.
acatech member Claudia Eckert, Chair of IT Security at the Technical University of Munich and Fraunhofer Institute for Applied and Integrated Security (AISEC), drew on the acatech publication “Cybersecurity. Current situation and future challenges” in the speech. A working group she leads came up with recommendations for how cybersecurity can be enhanced in Germany.
With advancing digitalisation, it is vital to prepare for professional cyber attacks, said Claudia Eckert. Moreover, cybersecurity is a fundamental element of trust in the digital systems with which society works day to day. The whole area of digital sovereignty is closely intertwined with cybersecurity: independent digital infrastructures, too, such as those being realised as part of the Gaia-X project, must be protected. This is the only way that self-determined and trustworthy activities in cyberspace are possible.
Definition of cybersecurity
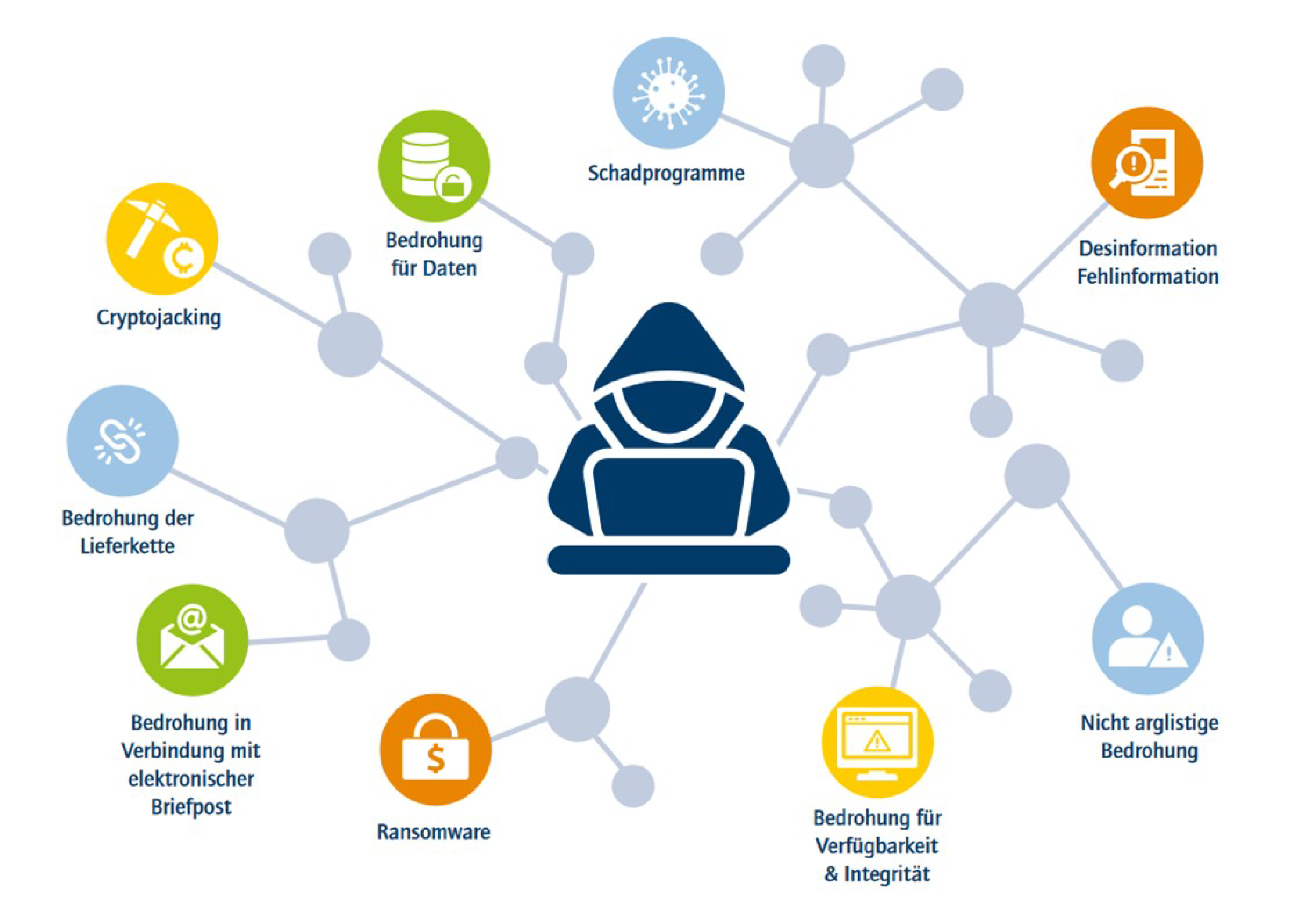
The goal of cybersecurity is thus on the one hand to protect data and information and on the other hand also to protect all communication and information systems used to process and transmit these data and information and the physical systems surrounding them. Since complete protection or fully achieving the protection goals cannot be guaranteed, it is always necessary to weigh up how the goals can be achieved to a reasonable extent at reasonable cost. Society must debate what is meant by “reasonable” in a particular context.
from: acatech publication Cybersecurity. Current situation and future challenges
Definition of digital sovereignty
from: acatech publication Cybersecurity. Current situation and future challenges
Whether we are in the car, working on the PC or on our smartphone in our free time, we all encounter IT-based products and systems every day, Claudia Eckert pointed out. They are also found in critical infrastructure for transport, healthcare, communication, the financial industry, energy and water supplies. IT-based products and systems are also components of company infrastructures such as bookkeeping, accounting, HR, production as well as digital services. More and more digital interfaces link products and infrastructures with the outside world. They process and share data – but these interfaces are the gateway that also allows them to be attacked or manipulated. This is where cybersecurity comes in with coordinated and organisational measures to protect IT-based systems and minimise damage, said Claudia Eckert.
Cybersecurity is therefore not solely a matter of the security technology but more so of organisation and enshrining the tenet of protection. Accordingly, the actions of the relevant stakeholders – policy makers, companies, science and citizens – must also be coordinated, said the IT researcher. To overcome the challenges of the present, the responsibilities of authorities must be clearly defined, powers must be pooled, a cybersecurity strategy must be clearly defined and it must be implemented exactly.
Cybersecurity in reality
Operators of critical infrastructures are obliged to report IT incidents or significant disruptions and to keep their IT security up to the state of the art. But what’s the reality?
Jörg Ochs, Head of Information Technology at Stadtwerke München, explained his organisation’s three-pronged strategy: prevention, detection and response. The most critical targets with electricity, gas, district heating and water are substations and control centres because they are visible to the public, said Jörg Ochs. For these, Stadtwerke München uses a multi-tiered concept with its own infrastructure and its own fibre-optic cables. In addition to the multi mesh active networks, low bandwidth copper networks provide additional protection. Furthermore, Stadtwerke München uses zero trust and microsegmentation. This means that the networks are built as small as possible so that, in the event of an attack, microsegments can relatively easily be turned on and off to contain the attack quickly.
Christian Sachgau, Head of Business Resilience at Deutsche Telekom Security GmbH, addressed the subject of resilience. There are direct safeguards that ensure that damage does not arise in the first place or is minimal. These include physical measures, backup power and cyber defence. If, despite all efforts, it is not possible to prevent a component or part of a business process from going down, the processes must be brought back up again as quickly as possible.
Deutsche Telekom also takes a three-tier approach to cybersecurity. First comes situation management, which monitors the cybersecurity situation and identifies the current threats in the cyber world. The relevance of these threats to Telekom systems is then analysed. Finally, courses of action can be developed from these findings. Christian Sachgau went on to say that legislation in the area of cybersecurity is very extensive and complex. Particularly the fact that the provisions vary from federal state to federal state and even from district to district is very challenging for large, national companies.
The discussion that followed was moderated by Marc-Denis Weitze. One issue raised concerned Europe’s digital sovereignty. acatech President Jan Wörner emphasised the importance of choosing the right international partners in this context. Claudia Eckert expressed her concerns about how dependent Germany currently is on foreign chip manufacturers. She said that it is important to pay attention to how these chips are being made. Rules must be put in place to facilitate a certain degree of traceability and thus to establish a secure base. We should also keep an eye on the supply chains, she said, and ask questions such as, “Where does the hardware come from?” “What goes into it?” We must have certainty that no undesirable manipulation has occurred.





